关于snort安装教程(爆肝两天,整合了网上所有资源,最终终于安装成功了!!!)
1. snort简介
Snort 是一个开源入侵防御系统(IPS)。
Snort IPS使用一系列规则来帮助定义恶意网络活动,并利用这些规则来查找与之匹配的数据包,并为用户生成警报。
肝了,兄弟们!!!废话不多说,直接上教程.
2. snort安装教程(Linux)
我装的是CentOS Linux,如果是Ubuntu的话那就太简单了,四句命令搞定,咱们这就以CentOS为例.
2.1) 咱们先来安装依赖文件.
yum -y install epel-release //需要epel源
yum -y install gcc flex bison zlib zlib-devel libpcap libpcap-devel pcre pcre-devel libdnet libdnet-devel tcpdump
yum -y install nghttp2
yum -y install glibc-headers g++ //后面安装ilbdnet-1.11.tar.gz需要
yum -y install openssl openssl-devel //后面安装snort 2.9时需要
2.2) 下载安装所需的压缩包,直接通过云下载就可以.
wget http://www.tcpdump.org/release/libpcap-1.9.0.tar.gz
wget http://prdownloads.sourceforge.net/libdnet/libdnet-1.11.tar.gz
# daq和snort,下载地址:https://www.snort.org/downloads/
wget https://www.snort.org/downloads/snort/daq-2.0.7.tar.gz
wget https://www.snort.org/downloads/snort/snort-2.9.20tar.gz
# daq 依赖文件,下载地址:http://luajit.org/download/
wget http://luajit.org/download/LuaJIT-2.1.0-beta3.tar.gz
上述代码直接copy就好,若出现wget not found 错误,使用 yum install wget即可解决.
2.3) 解压压缩包.
tar -zxvf libdnet-1.11.tar.gz
tar -zxvf libpcap-1.9.0.tar.gz
tar -zxvf daq-2.0.7.tar.gz
tar -zxvf snort-2.9.17.1.tar.gz
tar -zxvg LuaJIT-2.1.0-beta3.tar.gz
注:解压的压缩包默认都在root下.
# 先进入 libpcap-1.9.0 目录
cd libpacap-1.9.0
./configure
make && make install
cd ..
# 然后进入 libdnet-1.11目录
cd libdnet-1.11
./configure && make && make install
cd ..
# 接着进入 daq-2.0.7目录
cd daq-2.0.7
./configure && make && make install
cd ..
# 再然后进入 LuaJIT-2.1.0-beta3目录
cd LuaJIT-2.1.0-beta3
cd src
make
cd .. //返回上一层
make install
cd ..
# 最后进入snort-2.9.20目录
cd snort-2.9.20
./configure --enable-sourcefire
make && make install
cd ..
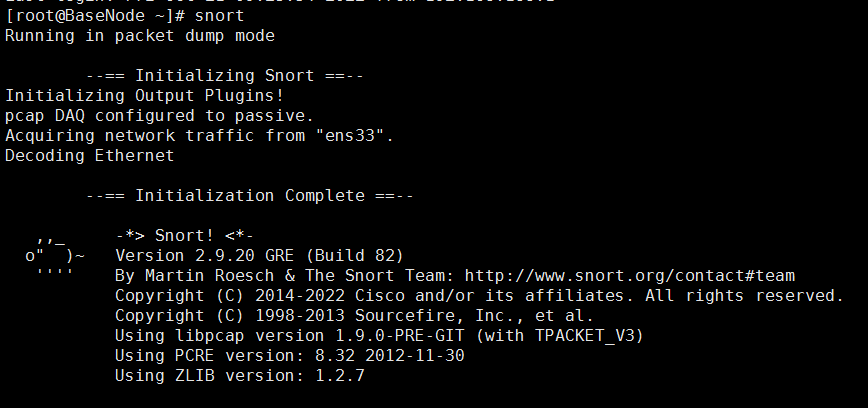
其实到这里就可以出现小猪图片了,但是我们还要进行配置一下.
3. 对snort文件进行配置,并添加规则.
# 首先创建snort配置(及规则)目录
mkdir -p /etc/snort/rules
# 创建运行需要目录
mkdir /usr/local/lib/snort_dynamicrules
# 首先将snort解压出来的下的默认配置文件复制到snort配置目录下
cp /root/snort-2.9.20/etc/gen-msg.map /root/snort-2.9.20/etc/threshold.conf /root/snort-2.9.20/etc/classification.config /root/snort-2.9.20/etc/reference.config /root/snort-2.9.20/etc/unicode.map /root/snort-2.9.20/etc/snort.conf /etc/snort/
# 下载社区规则并解压到规则目录
wget https://www.snort.org/downloads/community/community-rules.tar.gz
tar -zxvf community-rules.tar.gz -C /etc/snort/rules
# 注释掉所有默认要加载的规则文件
sudo sed -i 's/include \$RULE_PATH/#include \$RULE_PATH/' /etc/snort/snort.conf
# 启用社区规则文件
echo '' >> /etc/snort/snort.conf
echo '# enable community rule' >> /etc/snort/snort.conf
echo 'include $RULE_PATH/community-rules/community.rules' >> /etc/snort/snort.conf
# 重新设置snort.conf中的变量值
sed -i 's/var RULE_PATH ..\/rules/var RULE_PATH .\/rules/' /etc/snort/snort.conf
sed -i 's/var WHITE_LIST_PATH ..\/rules/var WHITE_LIST_PATH .\/rules/' /etc/snort/snort.conf
sed -i 's/var BLACK_LIST_PATH ..\/rules/var BLACK_LIST_PATH .\/rules/' /etc/snort/snort.conf
# 创建默认使用的白名单文件
touch /etc/snort/rules/white_list.rules
# 创建默认的黑名单文件
touch /etc/snort/rules/black_list.rules
# 创建默认自己设置的规则文件,其实我们注意了其他include只include了社区规则,所以这条根本没用这里只是意思一下
touch /etc/snort/rules/local.rules
# 测试配置文件是否有误
snort -T -c /etc/snort/snort.conf
4. snort的使用.
4.1) snort 嗅探模式.
snort -v
4.2) snort 记录模式.
# 该模式将截获的数据包记入文件(此处是当前log目录下),重点是-l
mkdir log
snort -dev -l ./log
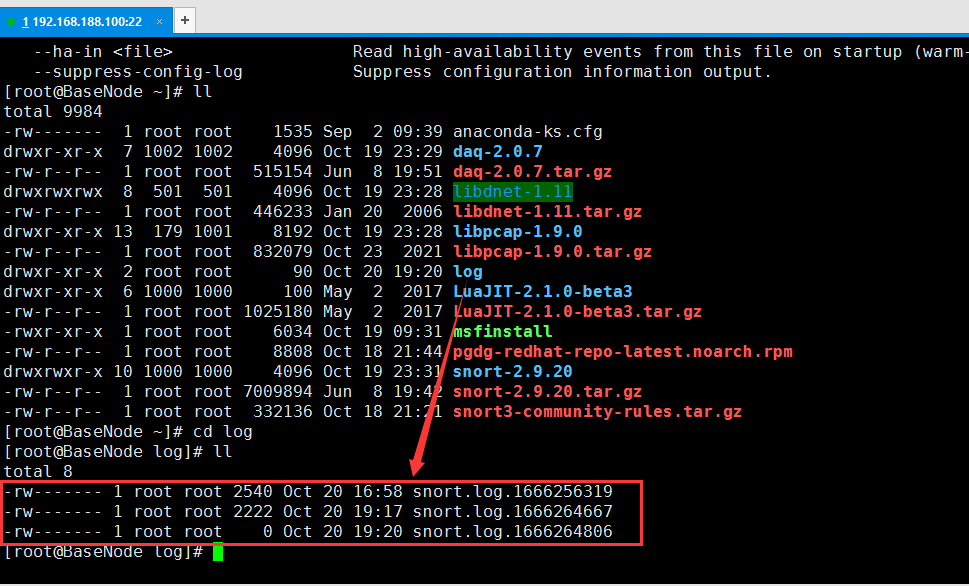
不一一展示了.
4.1) snort 网络入侵检测模式.
mkdir log
snort -dev -l ./log -h 192.168.1.0/24 -c /etc/snort/snort.conf
注:若出现classfication.config(0),则把etc/classification.config复制到/etc/snort/classification.config
好的,同学们,我已经被肝麻了,歇了.记得关注加点赞啊!!!拜拜


学到了学到了